Managing Your Award – Non-Financial
Advocacy and Outreach for Researchers
Review a foundation — take a survey: GrantAdvisor is a web service that "facilitates open dialogue between nonprofits and grantmakers by collecting reviews and comments on grant seekers’ experiences working with funders to encourage more productive philanthropy."
- Rethinking the Scientific Career: Chronicle of Higher Education, Oct. 3, 2017
- Cybersecurity for the travelling scientist: Nature, Aug. 2, 2017
- FASEB advocacy tools
- Public communication for researchers: Commentary article, Chronicle of Higher Education, July 17, 2017
- Speaking out as scientists: Nature, Dec. 21, 2016: So you want to change the world? by Nancy Baron
- Nature: Five top tips for getting your paper noticed
- Phys.org News: Despite advantages, cross-discipline research has a lower chance of receiving funding
- The Chronicle of Higher Education: Why Don't Young Scientists Get More Grants? Often They Don't Apply
- NSF: Researcher ethicist Q&A: 5 considerations for a transforming society
- Information about the AAU Handbook of Best Practices in Peer Review
- Want to get a politician to listen to science? Here’s some advice (Science, 2/17/19)
-
Help to shape policy with your science (Nature, 8/28/18)
Changes in Scope of Work
The Principal Investigator and the sponsor should discuss the need for any changes in the scope of work (SOW) before contacting OGCA. Common types of scope changes are changes in process, research direction, resources, and scheduling. A formal modification or amendment to the agreement may be required. The award's terms and conditions apply.
CUI GUIDANCE
University Security of Controlled Unclassified Information in Sponsored Research
GUIDANCE ON NIST 800-171 COMPLIANCE
Background:
National Institute of Standards and Technology (NIST) created information security standards to safeguard and distribute material or data deemed sensitive but not classified as Controlled Unclassified Information (CUI) in any Non-Federal Information Systems and Organizations doing research or procuring other goods and services for the US federal government. These standards (NIST 800-171) are included in Defense Federal Acquisition Regulation Supplement (DFARs) clauses (effective December 31, 2017) and are anticipated to be included in Federal Acquisition Regulation (FAR) clauses (in process, expected by end of 2019).
Under DFARs and FARs, Universities and federal agencies must jointly protect applicable agency assets and CUI. For institutions of higher education, information security (IS) and information technology (IT) investments should:
(i) be beneficial and relevant to the research enterprise.
(ii) balance the administrative burden for the conduct of research.
(iii) meet the needs and requirements of each agreed-upon research program and protocol.
Purpose:
The purpose of this document is to provide negotiation guidance, options, and strategies on how to work with federal agencies on required information security compliance for CUI. This guidance includes IT control alternatives for compliance and suggestions for projects where the compliance standards do not apply.
General Strategies and Approaches:
When applying for or accepting a research project that may include CUI or require NIST 800-171 compliance, always, as a first step, establish if CUI or data controls are needed and relevant for the scoped project, RFP, proposal, award, etc. For example, on April 24, 2018, DoD drafted guidance for procurements requiring implementation of National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171, Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations, for comment. Previously, universities, including UT System members, had noted a concern that CUI data types are often not fully defined by prospective awarding agencies ahead of proposal and/or in award documents, nor are CUI and CUI data types and standards always fully categorized or tailored to individual project research needs. Many universities asked that assessment be a required element. The updated DoD assessment chart includes prescribed identification of CUI (there is a series of “must require” and “must identify” security items, which any DoD agency must address in its Solicitation or RFP). This is expected to be approved in at least this form. While it complements university preference to avoid circumstances where unnecessary IS or IT protections are requested or required beyond existing provisions and security compliance requirements, we suggest that universities still be vigilant to identify on each’s own, that CUI requirements apply or not, as silence on requirements may not mean absence of CUI protection.
When NIST requirements are invoked, a complete assessment will need to be made by the University Principal Investigator (PI), in coordination with centralized IT and IS experts, to determine how his or her data handling and administrative practices match the specific requirements as stipulated by funding agency.
NIST 800-171 controls can be distilled to three categories:
Administrative practices – Policies, standards and procedures that the PI must maintain (e.g. access control, awareness or technical training).
Physical security – Guard against data loss in the event of theft or environmental conditions (flood, fire, etc.), or unauthorized access (e.g. cable locks, computer cages, etc.)
Technical safeguards – Guard against unauthorized access, data corruption, data loss, malware, etc. (e.g. implementing encryption, backups, RAID arrays, antivirus, NetIQ authentication, etc.)
The PI should consider the consequences of potential data loss or corruption (such as reputation, compromised or scooped discovery, loss of future funding, etc.) in determining whether to implement best practices beyond the minimum requirements for compliance.
Each University may be at a different stage in the process of determining whether certain centrally provided resources meet specific controls pursuant to requirements in NIST 800-171. This guidance and the attached decision trees for proposal and award stage negotiations may be helpful to engage in research projects as appropriate.
The high-level objective is to clarify the involvement/inclusion of data and information requiring safeguard or dissemination controls (e.g., CUI) as early as possible, preferably at proposal or even pre-proposal. If not addressed at application, University still has options at award or agreement stage. If the prospective or actual awarding agency has not taken responsibility for making the determination, the PI and sponsored project office should assume responsibility to ask questions, drive answers as needed, and negotiate to applicable standards and administrative burdens.
Ultimately, always be prepared to meet the stipulated minimum requirements. If you are fortunate to have a fully compliant solution that is of the highest level to cover all data transmittal, storage, generation and use, then deploy it. If you do not have that solution, then implement only the level of specific control requirement that applies, and then document any gaps if required by the DFARs to show how University will bring itself into required compliance.
Typically, there are 3 available options for University compliance, each with differing cost structures. Decision points are detailed in the table below.
- *Isolated: CUI applicable technical controls, work for anyone who wants to use the solution, without necessarily requiring compliance for entire University IT infrastructure (e.g., self-encrypting hard drives or portable drives, designated scheme-compliant server(s)).
- ** Partially Compliant: Solution available for University-wide use by any PI, but which will be tailored as a single, one-off option (e.g., use resources as narrowed to project proposal or project at hand, including a PI-specific plan of action and milestones (sometimes abbreviated by industry consultants as POAM), to address any gaps or deficiencies to correct).
- ***Fully compliant: Third party compliant options or outside collaborator systems, or University internal or affiliated (such as TACC) systems. In some instances, the funding agency may be able to provide resources to the PI.
Detailed Options, Track Decision Tree:
The following chart shows more detailed information to suggested processes and tips, and selected NIST CUI standards for institutions to consider.
PROPOSAL STAGE
|
DETAILED OPTIONS, REFER TO APPLICABLE DECISION TREE |
NIST STANDARDS (SP 800-171); SELECTED COMMENTS |
|
Ask if controlled data (e.g., CUI) is applicable to the project. If the prospective awarding agency has not taken responsibility, University PI should assume responsibility to ask questions, drive answers as needed.
If planned data exchanges or storage DOES require controlled data compliance, AND University complies:
If planned data exchanges or storage DOES NOT require controlled data compliance:
If planned data exchanges or storage DOES require controlled data compliance AND University CANNOT or does NOT comply in whole or in part:
|
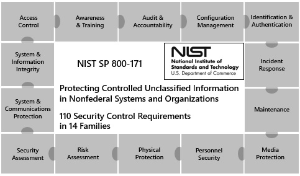
National Institute of Standards and Technology: “Protecting Controlled Unclassified Information (CUI) in Nonfederal Information Systems and Organizations” (2016) – regulates safeguarding and dissemination of CUI. These ‘cyber security’ protections and requirements also map to ISO/IEC 27001 controls, which make compliance more feasible. 800-171 (Rev 1 is current as of this guidance) has 14 control families with (now) 110 requirements and is derived from 800-53 (which is intended for federal information systems and has 18 control families with 600+ requirements). CUIs and CUI data types are often not defined in award documents, nor are the CUIs often categorized. Institutions typically already comply with significant IS rules. |
|
|
|
AWARD STAGE |
|
|
If University has not had the opportunity to review, or has not reviewed and considered data use at proposal stage, or has not been addressed, but has been fortunate to receive an award anyway: ALWAYS:
If University CANNOT meet all requests:
|
|
Cost Accounting Standards
Researchers at University of Alaska Fairbanks (UAF) have a variety of cost accounting standards they must adhere to when spending extramural funds, including Office of Management and Budget (OMB) – Uniform Guidance and University of Alaska/UAF charging practices.
Because the majority of UAF’s research funding comes from the federal government, most of our cost accounting standards are based on federal regulations. These are listed in circulars provided by the Office of Management and Budget (OMB) in the executive branch of the federal government.
All federal sponsor policies that govern grant management (such as the NIH Grants Policy Statement) are based on the OMB Uniform Guidance, which establishes principles for determining allowability of costs applicable to grants, contracts and other agreements with educational. Per Uniform Guidance, all costs in the budget should be allocable, reasonable and allowable.
- Allocable costs are clearly associated with the particular project. For example, chemicals purchased for use on a specific project should only benefit that project. Restocking general chemical supplies used for a variety of purposes would benefit many projects and may not be easily allocated to individual projects. Consider whether the cost will be incurred solely to advance the work under the sponsored agreement. For example, travel costs incurred for the Principal Investigator to obtain data on the topic of the research would generally qualify, but travel costs to attend a conference on a topic not related to the research would not.
- Reasonable costs would generally be accepted as necessary per a “prudent” person’s review. For example, the purchase of a laptop computer for field research by a graduate student researcher on the project would generally be accepted as reasonable, while the purchase of a laptop for non-project related coursework by a graduate student researcher would not.
- Allowable costs are permitted by institutional and sponsor regulations and are consistent with UA/UAF charging practices. There are some costs which are specifically prohibited from being charged to a sponsored project, such as alcoholic beverages, advertising, lobbying or entertainment charges. These are known as "unallowable" costs. It is important to ensure that a cost is allowable before including it in a proposal.
The Federal Cost Accounting Standards Board (CASB) has the following four cost accounting standards applicable to University of Alaska/UAF which help to clarify what costs must be treated consistently.
- Estimating, Accumulating and Reporting Costs: In order to permit comparisons of estimates to actual costs, the expenditure classifications used to estimate costs in contract and grant proposals must be consistent with those used to accumulate and report costs.
- Allocating Costs Incurred for the Same Purpose: Costs incurred for the same purpose, in like circumstances, must be treated consistently as either direct or indirect costs.
- Accounting for Unallowable Costs: Unallowable costs must be identified and accounted for independently from allowable costs.
- Cost Accounting Period: Consistent use of the same cost accounting period for purposes of estimating, accumulating and reporting costs is required. At the University of Alaska, this is the Fiscal Year (FY) which occurs July 1- June 30
Cybersecurity Maturity Model Certification (CMMC)
This information pertains to UAF research activities that intend to or currently participate in research sponsored by agencies, offices and commands under the US Department of Defense.
- CMMC Level 1 -Security Plan Template Thanks to University of Washington for the template.
What You Need To Know:
Federal Government and Department of Defense related research contracts with the DFARS 252.204-7012 clause.pdf and Export Control (ITAR/EAR), have required compliance with the Cybersecurity Capability Maturity Model (CMMC) Level 3 that includes the NIST SP 800-171.pdf security controls to safeguard Controlled Unclassified Information (CUI). CUI is data that requires protection through dissemination controls pursuant to and consistent with applicable law, regulations and government-wide policies but is not classified.
CMMC applies to CUI shared by or through the federal government with a nonfederal entity. As a higher educational institution, UAF is a non-federal entity. There are 130 technical and operational controls specified by the CMMC/NIST standard and ITS has made every effort to reduce the compliance efforts for the Principal Investigator (PI).
The Secured Research Infrastructure (SRI) was developed with the intent of meeting the security control requirements while also reducing the workload on the PI to the smallest amount practical while still ensuring compliance. This solution meets 3 key design principles:
- The controls requirements established by the CMMC/NIST standard are complex. Each research project will be reviewed for its specific technical requirements to properly safeguard CUI. Ensuring controls consistency reduces the time to bring a new project into the environment and increases the ability to ensure compliance.
- The system needs to provide the ability for researchers, whenever practical, to access and work with their data anywhere and have the environment be supported centrally.
- The security controls should be provided centrally. University of Alaska Records and Information Management has made significant investments in our enterprise level security infrastructure and operational processes that enable us to protect CUI using centrally supported tools with more capabilities that can be provided locally.
The CMMC is a program established by the United States Department of Defense (DoD) to standardize security practices and processes intended to protect Federal Contract Information (FCI), 48 CFR § 52.204-21 and/or Controlled Unclassified Information (CUI), Executive Order 13556, associated with DoD-funded research.
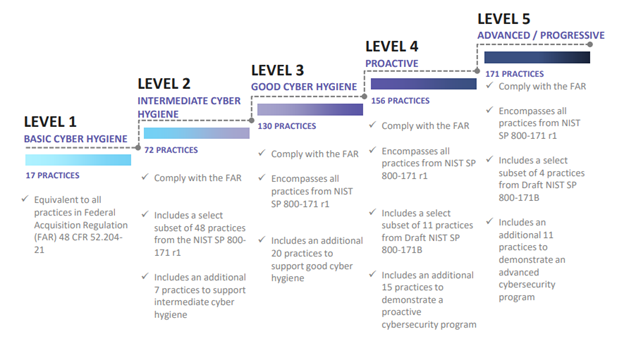
The CMMC model framework organizes processes and cybersecurity best practices into a set of 17 capability domains and 5 levels of maturity in practices and processes. CMMC involves an independent third-party assessment (from DoD approved assessors) of an organization’s compliance at a specified maturity level.
Beginning November 30, 2020, DoD will incorporate requirements for CMMC into selected Requests for Proposals (RFPs), Requests for Information (RFIs), and research contracts. By October 1, 2025, all DoD contract awards will require CMMC certification to Level 1 at a minimum. CMMC requirements will not be applied retroactively to existing contracts.
The CMMC combines cybersecurity standards and best practices from multiple sources and references:
- CMMC Level 1, the minimum maturity level for protecting FCI, addresses practices from Federal Acquisition Regulations (FAR) 52.204-21.
- CMMC Level 2 is a progression level from Level 1 to Level 3 and contains subset of security requirements specified in NIST 800-171 for protection of CUI.
- CMMC Level 3, the minimum maturity level for protecting CUI, includes all of the practices from National Institute of Standards and Technology Special Publication (NIST SP) 800-171r1 as well as others.
- CMMC Levels 4 and 5 incorporate a subset of the practices from Draft NIST SP 800-172 plus others, and are intended to provide enhanced security to critical technologies and acquisition programs.
Defense Federal Acquisition Regulations (DFARS) clauses that implement CMMC:
- DFARS 252.204-7012, ‘Safeguarding Covered Defense Information and Cyber Incident Reporting’
- DFARS 252.204-7019, ‘Notice of NIST SP 800-171 DoD Assessment Requirements’
- DFARS 252.204-7020, ‘NIST SP 800-171 DoD Assessment Requirements’
- DFARS 252.204-7021, ‘Cybersecurity Maturity Model Certification Requirements’ (through 9/30/2025)
Interim DFARS Rule:
The interim Defense Federal Acquisition Regulation Supplement rule (DFARS 252.204-7021) is a major rule change which went into effect on 11/30/2020. This rule change adds three new clauses to the original one which mandates compliance with NIST 800-171 for entities handling CUI. Two of the new clauses introduce and establish the CMMC requirements. The third one requires companies handling CUI to complete a self-assessment or Basic Assessment. This must be done using the DoD Assessment Methodology and a score must be generated. This score along with the gap remediation date into the Supplier Performance Risk System (SPRS). When the contract is awarded, a DoD contracting officer will verify the uploaded score. The DoD will then perform risk-based assessments to determine which company will be awarded the contracts.
Process of the Principal Investigator:
The PI of the research project should have already met with OGCA and together determined that the research must comply with CMMC/NIST SP 800-171 standards. In addition, the PI should have already met with the Office of Research Integrity’s Export Control Officer and completed a Technology Control Plan (TCP).
What You Need To Do:
If you plan to respond to a DoD RFP or RFI that includes the DFARS clauses above, please note the following:
- You must have adequate cybersecurity measures in place according to the Cybersecurity Maturity Level established by the DoD. The required Level will be noted in the RFP or RFI.
- You must complete a self-assessment of your security implementation and file the results in the DoD Supplier Performance Risk System (SPRS) by the time of the contract award. (See ‘Resources’ section below for more information on SPRS).
- Implementation of these measures will eventually need to be certified by an accredited third party that is external to the UAF.
- You may include the costs to implement these measures as a direct cost in your proposal budget, with proper substantiation of cost.
FAQs
Where do I find out more about the DoD CMMC?
The Office of the Under Secretary of Defense for Acquisition & Sustainment has a very informative website on Cybersecurity Maturity Model Certification.
- The UA Chief Information Security Officer (CISO) and University of Alaska Records and Information Management maintains information for complying with the CMMC Requirement.
How will CMMC work?
The DoD will require CMMC certification by a third party prior to any contractor winning a DoD contract. The DoD has appointed a non-profit group, the CMMC Accreditation Body (AB), to oversee the certification process. The AB will certify third-party inspectors. These Certified Third-Party Assessment Organizations (C3PAO) will then certify companies against the different CMMC standards/levels. The C3PAO inspectors will provide companies’ certification levels to the AB for tracking and provision to the DoD. The AB will not make CMMC certification levels publicly available.
How will CMMC impact Alaska companies?
The new CMMC program will require certification for all companies currently doing business with the DoD or who want to do business with DoD. This group of affected companies includes companies supporting the DoD through contracts and subcontracts including services. The DoD estimates that over 300,000 companies will eventually need to be certified. All companies will need at least CMMC Level 1 certification.
When will CMMC be rolled out?
DoD published the initial set of CMMC standards on January 31, 2020 and quickly followed up with an update in March 2020 (see CMMC Model 1.02). On November 30, the DFARS 252.204-7021 clause went into effect and states by October 1, 2025, all entities* receiving DoD contracts and orders will be required to have the CMMC Level identified in the solicitation (minimum will be a CMMC Level 1). Between now and then, CMMC will be rolled out on new RFPs. It is estimated that 60% of the DIB will require Level 1 certification and 30% will require Level 3 certification.
*only exceptions are commercially available off-the-shelf (COTS) items or those valued at or below the micro-purchase threshold.
How will CMMC compliance be different from compliance with NIST SP 800-171 through DFARS 252.204-7012?
CMMC Levels 1-3 encompass the 110 security requirements specified in NIST SP 800-171 rev1. CMMC incorporates additional practices and processes from other standards, references, and/or sources such as NIST SP 800-53, Aerospace Industries Association (AIA) National Aerospace Standard (NAS) 9933 “Critical Security Controls for Effective Capability in Cyber Defense”, and Computer Emergency Response Team (CERT) Resilience Management Model (RMM) v1.2. Unlike NIST SP 800-171, the CMMC model possesses five levels. Each level consists of practices and processes as well as those specified in lower levels.
How will CMMC impact subcontractors?
At a minimum, all subcontractors will be required to carry CMMC Level 1 Certification to continue to participate in DoD contracts so long as your company does not solely produce COTS products and the contract is not below the minimum purchase limit. Additionally, a prime contractor may require Level 3 Certification for a contract while subcontractors may require different levels of certification. Prime contractors will work with contracting officers to determine the CMMC levels required for subcontractors. The process to determine subcontractors’ CMMC certification requirements is still evolving.
What will CMMC cost?
The DoD will cover the costs associated with CMMC, including CMMC audits and the efforts undertaken to prepare for them. This is part of the DoD's emphasis of the mission critical nature of cybersecurity to the country's defense.
What is NDAA 889?
The National Defense Authorization Act Section 889 (NDAA 889) is an amendment to the Federal Acquisition Regulation (FAR). It prohibits government agencies from entering, extending, or renewing a contract with an entity using equipment, system(s), or service(s) classified as covered telecommunications and video surveillance equipment or services.
The US Government updates this rule periodically. In addition to the list of companies below and their subsidiaries and affiliates, the list of prohibited entities now includes other entities believed to be owned, controlled by, or connected to either the People's Republic of China or the Russian Federation.
- Huawei Technologies Company
- ZTE Corporation
- Hytera Communications Corporation
- Hangzhou Hikvision Digital Technology Company
- Dahua Technology Company
UAF will have to certify that any equipment, systems, or services used in research or other work with the Government do not contain any covered telecommunications and video surveillance equipment or services covered under NDAA 889. Purchasing equipment and services from these vendors could jeopardize UAF's ability to receive federal funding.
How does it affect UAF?
Individuals or groups seeking to do business with the DoD should:
- Review the Request for Information (RFI) and Request for Proposal (RFP) for the appropriate CMMC level.
- Ensure the appropriate cybersecurity measures in place for the required CMMC level.
- Possess the appropriate level of CMMC certification before accepting an award.
- Ensure compliance with the NDAA 889 regulation.
- Comply with the interim DFARS rule.
Is Fundamental Research exempt from CMMC?
There is no exemption from CMMC for fundamental research.
The specific IT security requirements apply to DoD Contracts handling:
- Federal Contract Information (FCI)
- Controlled Unclassified Information (CUI)
UAF fundamental research projects can include FCI or CUI.
How do I build in the cost of becoming certified as a direct cost in my proposal?
The DoD states the cost of certification will be considered an allowable, reimbursable cost. In order to integrate into your budget, follow any instructions in the RFP on this, and obtain estimates of cost, so you can substantiate charging to the sponsor. This includes obtaining quotes on system upgrades and the cost of obtaining a third-party assessment, if that is your situation.
When will university-based labs and other research facilities conducting DoD sponsored research need to be CMMC certified?
Don’t wait. Effective Nov. 30, 2020, DoD intends to add CMMC certification requirements to its Requests for Proposals (RFPs), starting with approximately 15 procurements for critical DoD programs and technologies, such as those associated with nuclear and missile defense. DoD estimates that each of the 15 primes will have an average of 100 subcontractors, and thus approximately 1,500 primes and subcontractors will be affected by fall 2021.
If you are a PI/department or other organizational unit at UAF intending to respond to a DoD RFP in the next several months, or you regularly pursue DOD contract funding or collaborations with defense contractors, you should prepare to submit your IT security plan, self-assessment, and other required documentation into the DoD SPRS system for Level 1 (FPI) or Level 3 (CUI). Don’t wait until the RFP is released.
Keep track of costs to obtain the IT Level of Security. Include the associated costs with your i proposed scope of work when an RFP becomes available.
Will the CMMC requirement apply to DoD grants, in addition to contracts?
At this time, it is understood this will apply to DoD contract funding only, and only pertains to the project when the RFP/RFI includes a statement as to the CMMC Level that will apply. However, OGCA is monitoring all DoD awards as they are made.
Resources:
CMMC Level 1 System Security Plan Template
CMMC Level 1 System Security Plan Template (docx) to assist in documenting the security controls necessary to meet the CMMC Level 1 requirements. Thanks to University of Washington for the template.
Supplier Performance Risk System (SPRS) ‘Quick Entry Guide’
https://www.sprs.csd.disa.mil/pdf/NISTSP800-171QuickEntryGuide.pdf
CMMC:
NDAA 889:
- https://www.federalregister.gov/documents/2020/07/14/2020-15293/federal-acquisition-regulation-prohibition-on-contracting-with-entities-using-certain
- https://www.federalregister.gov/documents/2021/01/15/2021-00612/defense-federal-acquisition-regulation-supplement-covered-defense-telecommunications-equipment-or
Interim DFARS rule:
- https://www.acq.osd.mil/dpap/dars/change_notices.html
- https://www.federalregister.gov/documents/2020/09/29/2020-21123/defense-federal-acquisition-regulation-supplement-assessing-contractor-implementation-of
- https://ocd-tech.com/2021/01/18/cmmc-interim-rule-explained/
Articles:
- Federal cybersecurity requirements in higher education – April 2, 2021
- Higher Education Research, Cybersecurity and CMMC Compliance – Educause
- Analysis of the Cybersecurity Maturity Model Certification (CMMC) – Indiana University
Freedom of Information Act (FOIA)
The Freedom of Information Act (FOIA) of 1967, 5 U.S.C. 552, requires federal funding agencies to release certain grant documents and records requested by members of the public, regardless of the intended use of the information. These policies and regulations apply to information in the possession of the federal agency and do not require grantees or contractors under grants to permit public access to their records. The regulations also indicate types of information that are generally exempt from release.
The Freedom of Information Act (FOIA) provides the public the right to request access to records from any Federal agency. It is often described as the law that keeps citizens in the know about their government. Federal agencies are required to disclose any information requested under the FOIA unless it falls under one of nine exemptions which protect interests such as personal privacy, national security, and law enforcement.
The following types of information/materials will generally be released in response to an FOIA request, whether the materials are maintained in paper or electronic format:
- Funded applications;
- Pending and funded non-competing continuations;
- Grant progress reports; and
- Final reports of any audit, survey, review, or evaluation of grantee performance that have been transmitted to the grantee.
The following types of information/records will generally be withheld in response to an FOIA request:
- Pending competing grant applications;
- Unfunded new and competing continuations and competing supplemental applications;
- Financial information regarding a person, such as salary information pertaining to project personnel;
- Information pertaining to an individual, the disclosure of which would constitute a clearly unwarranted invasion of personal privacy;
- Pre-decisional opinions expressed by Government officers, employees, or consultants in inter- or intra-agency memoranda or letters;
- Evaluative portions of site visit reports and peer review summary statements, including priority scores;
- Trade secrets and commercial, financial, and otherwise intrinsically valuable items of information that are obtained from a person or organization and are privileged or confidential;
- Information that, if released, would adversely affect the competitive position of the individual or organization; and
- Patent or other valuable commercial rights of the individual or organization
If the federal funding agency receives an FOIA request and has substantial reason to believe that information in its records could reasonably be considered exempt, the appropriate agency FOIA Officer will notify the grantee before the information is released, allowing the grantee an opportunity to identify potentially patentable or commercially valuable information that should not be disclosed.
After agency consideration of the grantee's response, if any, the grantee will be informed of the agency's decision as to what documents will be released and to whom. If a document contains both disclosable and non-disclosable information, the non-disclosable information will be deleted by a designated agency FOIA Officer, and the balance of the document disclosed.
Federal agencies are required to respond to a FOIA request within 20 business days, excluding Saturdays, Sundays, and legal holidays. For the Privacy Act, the time limit is 10 business days. This period does not begin until the request is actually received by the FOIA office of the Federal agency.
In addition, a Federal agency may receive a request (not identified as FOIA) for a copy of a grant application (proposal). The awardee institution will be contacted by the Federal agency regarding this request, informing that the proposal will be released with certain person and salary data redacted from the proposal application. These requests are not required to follow the 20-day limitation response time as set forth in the FOIA Act.
All FOIA requests are coordinated with General Counsel and OGCA.
Harassment and Discriminations Protections
The University of Alaska Fairbanks (UAF) has empowered the Office of Rights, Compliance and Accountability (ORCA) to investigate and resolve complaints of employment discrimination, harassment, or retaliation prohibited by law or University policy. ORCA works with the University community to implement and uphold policies and practices that are consistent with these federal and state mandates, as well as the existing University policies regarding equal access, equal employment, and educational opportunity for all persons. Visit the ORCA website for more information.
The UAF is committed to creating and maintaining an educational, research, working, and living environment free from all forms of unlawful harassment and sexual misconduct. The University has created policies and procedures that describe the community standards of conduct as well as the procedures for grievances and complaints alleging violations of its discrimination and harassment policies.
In addition to University policy, Federal and State sponsors of UAF’s research have notification and reporting requirements related to sexual harassment, harassment, sexual assault, and discrimination. Many of these sponsors have recently issued rules and guidance regarding these requirements and the importance of adhering to them.
Federal Agency Specific Guidance:
National Science Foundation (NSF)
NSF Requirements
On September 21, 2018, NSF published in the Federal Register a Final Notice of a new award “term and condition regarding sexual harassment, other forms of harassment, and sexual assault.” That term and condition requires the University to notify NSF promptly of findings or determinations of “sexual harassment, other forms of harassment, or sexual assault” concerning an NSF-funded principal investigator (PI) or Co-PI, as well as of any interim administrative actions imposed by the University (e.g., administrative leave or curtailment of certain University duties) relating to any finding, determination, or investigation of an alleged violation by a PI or Co-PI of the University’s policies relating to harassment and assault.
The term and condition is effective for NSF awards and amendments made on or after October 22, 2018.
UAF has established procedures that comply with these requirements. Please contact OGCA with questions or for more information.
NSF-Sponsored Conferences
NSF’s Proposal and Award Policies and Procedures Guide (PAPPG) (effective February 25, 2019) sets forth a requirement that conference proposers have “a policy or code-of-conduct that addresses sexual harassment, other forms of harassment, and sexual assault, and that includes clear and accessible means of reporting violations of the policy or code-of-conduct.” Notably, “[t]his policy or code-of-conduct must be disseminated to conference participants prior to attendance at the conference and made available at the conference itself.”
For more information on applicable UAF policies and how UAF can assist researchers with complying with NSF conference requirements, please contact OGCA.
NSF Agency Information
Important Notice No. 144: Harassment (Feb. 8, 2018)
NSF, Office of the Director, Sexual Harassment
NSF Term and Condition: Sexual Harassment, Other Forms of Harassment, or Sexual Assault
National Institutes of Health (NIH)
NIH Requirements
NIH requires that grantees have “policies and practices in place that foster a harassment-free environment.” With respect to this rule, NIH has stated the following:
“NIH expects that grantee institutions:
- develop and implement policies and practices that foster a harassment-free environment;
- maintain clear, unambiguous professional codes of conduct;
- ensure employees are fully aware and regularly reminded of applicable laws, regulations, policies, and codes of conduct;
- provide an accessible, effective, and easy process to report sexual harassment, and provide protection from retaliation;
- respond promptly to allegations to ensure the immediate safety for all involved, investigate the allegations, and take appropriate sanctions; and
- inform NIH of administrative actions that removes senior/key personnel on an NIH award.”
UAF has established policies and procedures that meet and provide mechanisms for researchers to comply with these expectations. Please contact OGCA for more information.
NIH Training Grant Applications
In addition to these expectations, NIH has established parameters relating to harassment that are specific to certain types of grants. For Institutional Training (T) Applications (T15, T32, T34, T35, T36, T37, T90/R90, TL1, TL4), NIH requires as follows:
“As part of the Letters of Support on the PHS 398 Research Training Program Plan form, applications currently include a description of the applicant institution’s commitment to the planned program in order to ensure its success . . . In the same letter, applicants should include a description of the institutional commitment to the following areas:
(i) ensuring that proper policies, procedures, and oversight are in place to prevent discriminatory harassment and other discriminatory practices;
(ii) responding appropriately to allegations of discriminatory practices, including any required notifications to OCR . . .; and
(iii) adopting and following institutional procedure for requesting NIH prior approval of a change in the status of the Program Director/Principal Investigator (PD/PI) or other senior/key personnel if administrative or disciplinary action is taken that impacts the ability of the PD/PI or other key personnel to continue his/her role on the NIH award described in the training grant application . . .
The signed letter should be on institutional letterhead from an Authorized Organizational Representative (AOR), or other key institutional leader with institution-wide responsibilities.
UAF has made the required institutional commitments. Please contact OGCA for more information or for assistance with or questions regarding Letters of Support.
NIH Conference Grants (R13)
NIH requires that “NIH recipients of conference grant (‘R13’) funding must take steps to maintain a safe and respectful environment for all attendees by demonstrating an institutional commitment to ensuring that proper policies, procedures, and oversight are in place to prevent discriminatory harassment and other discriminatory practices.”
UAF has made the required institutional commitments. Please contact OGCA with questions about this requirement or assistance with conference grants.
NIH Agency Information
All About Grants Podcast on NIH Anti Sexual Harassment Policies Dr. Jodi Black (August 8, 2019)
How to Notify NIH about a Concern that Sexual Harassment is Affecting an NIH-Funded Activity at a Grantee Institution (June 14, 2019)
Update on NIH’s efforts to address sexual harassment in science (Feb. 28, 2019)
NIH Director's statement on changing the culture of science to end sexual harassment (Sept. 17, 2018)
NIH Anti-Sexual Harassment Statement, including links to regulations, policy, and FAQs
Anti-Sexual Harassment: for NIH Awardee Organizations and Those Who Work There
National Aeronautics and Space Administration (NASA)
In January 2016, NASA Administrator Charles Bolden published a letter to grantee institutions running NASA-funded programs regarding harassment policies, which stated as follows:
“As a leader in the fields of science, technology, engineering and mathematics (STEM), NASA endeavors to make our collaborations with our grant recipient institutions as productive and successful as possible in all facets of our shared objectives. This means that we seek not only the most innovative and cutting-edge scientific and technological research from our grant recipients, we also expect strong efforts to create and sustain welcoming educational environments. We view such efforts not as “something nice to do” if the time can be spared, or something that human resources or the [equal opportunity] offices are responsible for, but rather as an integral and indeed necessary aspect of all educational program environments.
Let me be perfectly clear: NASA does not tolerate sexual harassment, and nor should any organization seriously committed to workplace [equal opportunity]. Science is for everyone and any behavior that demeans or discourages people from fully participating is unacceptable.”
NASA Proposed Requirements
Following on this commitment, NASA published a notice in the July 10, 2019 Federal Register entitled “Reporting Requirements Regarding Findings of Harassment, Sexual Harassment, Other Forms of Harassment, or Sexual Assault,” seeking public comment on a proposed rule that would institute a new term and condition in NASA awards requiring reporting of sexual harassment, other forms of harassment, and sexual assault.
The Notice explained NASA’s policy objective as follows: “The implementation of new reporting requirements is necessary as NASA seeks to help ensure research environments to which the Agency provides funding are free from sexual harassment, other forms of harassment, and sexual assault.”
Similar to NSF, the new term and condition would require NASA-funding recipients to report (1) findings and determinations regarding the PI or Co-PI that demonstrate a violation of the recipient’s policies or codes relating to harassment and assault and/or (2) administrative action relating to any finding, determination, or investigation of an alleged violation by a PI or Co-PI of the recipient’s policies relating to harassment and assault.
Comments in response to the Notice were due no later than August 16, 2019, and the new requirements will likely become effective in the fall of 2019. OGCA will provide updates as they become available.
NASA Agency Information
NASA Administrator communicates harassment policies to grantees (Jan 15, 2016)
Compliance Requirements for NASA Grantees
Harassment and Discrimination Reporting for NASA Employees, Contractors and Grantee Beneficiaries
Inappropriate Foreign Influence Checklists
As one of the world's leading research institutions, University of Alaska Fairbanks (UAF) seeks out a wide range of mutually-beneficial international collaborations. Additionally, UAF welcomes talented scientists and scholars from around the globe. These individuals strengthen its research and teaching activities as well as its commitment of service to the nation and humanity.
Over the last years, U.S. government representatives on both sides of the aisle as well as federal law enforcement agencies have expressed growing concern about “foreign influence”, or security threats posed to the United States by actors representing non-U.S. interests. “Foreign influence” can be a concern in different arenas of American society, including the U.S. research enterprise. UAF takes these concerns seriously. At the same time, UAF recognizes that language is important here. Given our institutional commitment to equal opportunity and global engagement, we have not internally adopted the term “foreign influence” used by the U.S. government. We instead refer to this activity as “inappropriate foreign influence”.
Many of UAF’s major federal sponsors have issued guidance regarding inappropriate foreign influence. Links to sponsor-specific guidance appear below. UAF has developed a set of guidance designed to guide the formulation of practices related to inappropriate foreign influence, while upholding the University’s core values of openness and respect.
The issues raising concern for agencies and federal funders can be summarized as:
- Failure to fully disclose information on outside activities: Failure by some researchers to fully disclose substantial or overlapping commitments to or resources from organizations outside their “home” institution, including significant professional or employment-related engagements such as appointments at foreign institutions, etc. via their institutions’ internal disclosure processes and/or in sponsored program proposals or progress reports.
- Loss of intellectual property: A number of reported instances of unauthorized removal of data from research laboratories in the U.S. have resulted in the loss of intellectual property including, in some instances, publication of the misappropriated data before the U.S. scientists and institutions from which it was taken were able to publish.
- Noncompliance with regulatory requirements: U.S. export control laws and regulations establish a set of requirements for transfer of technology and data to foreign countries and/or foreign nationals, including persons in the U.S., in order to protect the national and economic security of the U.S.
- Breaches of integrity in the peer review process: Sharing of confidential information in grant applications with unauthorized parties by peer reviewers, including foreign entities, or otherwise inappropriately attempting to influence federal agencies’ funding decisions.
Researchers and research administrators at UAF should confirm current disclosure requirements, ask questions as appropriate, and work to keep disclosures up to date. Disclosure requirements currently vary between sponsors. Please see specific sponsor guidance below. If in doubt, investigators should contact their OGCA for disclosure assistance or further guidance.
International Relationships /Foreign Influence and Activities
The U.S. Government, including members of Congress and federal agencies, has expressed serious concerns regarding inappropriate influence by foreign entities, government, or individuals on U.S. institutions and researchers. Key concerns of foreign influence are:
- Inappropriate or inadvertent sharing of proprietary information, intellectual property, or data of grant applications, unpublished research, or technologies.
- Sharing of confidential information by researchers serving as peer reviewers of grant applications.
- Failure of researchers to disclose substantial support from outside activities or foreign organizations in grant applications Current & Pending forms. Particularly, there are concerns regarding the failure to follow federal agency requirements to disclose foreign components or foreign collaborations in progress reports or ongoing awards.
- Foreign employment arrangements
- Foreign grant support that may overlap or over-commit researchers
- Significant foreign financial Conflicts of Interest
Several federal agencies have indicated that failure to disclose foreign relationships and activities may jeopardize eligibility for future funding.
The concerns of foreign influence are often limited to the inappropriate and intentional actions of a few. Foreign Influence concerns are mitigated by informing researchers of institutional and federal disclosure requirements and best practices to prevent inadvertent or premature sharing of sensitive research data to foreign entities.
All employees should understand that Foreign Influence in research is an issue regarding the orchestrated actions of foreign governments and not about profiling any ethnicity or the activities of our employees.
The CITI Program has a module called The Undue Foreign Influence. UAF researchers, staff and students are encouraged to take the course for additional understand.
The following information provides guidance and resources to remind researchers of their disclosure requirements to federal agencies and the university.
Recognized benefits of Foreign Research Collaborations
U.S. academic research institutions are open to people of all backgrounds and nations. This openness is not just a matter of principle, it has created a national competitive advantage by attracting talented people from around the world to the U.S. The benefits of this approach and underlying policies that have enabled it are powerfully demonstrated by the level of academic excellence in the U.S. and our standard of living.
UAF strongly supports foreign collaborations for the benefits of student recruitment and talent, access to unique research facilities and programs, research funding opportunities, research dissemination, and publication opportunities. Therefore, the intention of this guidance and disclosure information is not to prevent or limit foreign collaborations, rather it is for the purpose of awareness of concerns foreign influence presents and its mitigation by providing assistance to resources and the requirements for researcher transparency.
Targeted or Sensitive Research Areas of Foreign Influence
Research (data, technologies, or materials) can generally be categorized as follows:
- Open Research: Research that is public or publishable without restriction (most common at universities).
- Research Intellectual Property: Research that has high economic value or potential (e.g. Patent Applications or Know-how). Publication may be delayed or withheld for commercialization purposes.
- Controlled, Controlled Unclassified (CUI), or Sensitive Research: Research that is not public, is governed under publication restrictions, or is not fundamental. This includes data or technologies that may require a license under the Export Administration Regulations (EAR), the International Traffic in Arm Regulations (ITAR) (research that may involve a military application) or that is deemed confidential under a non-disclosure agreement. Controlled Unclassified Information (CUI) is information provided by or deemed as CUI by a federal agency that must follow specific data or security standards.
- Classified Research: The University is not authorized to store or transfer research designated as Classified by the U.S. government. However, UAF Faculty may be authorized to conduct classified research at a secured facility. UAF does not possess any classified research.
For all university research, researchers have a self-interest to be diligent in safeguarding and managing research data for its integrity and to prevent Intellectual Property theft (academic or commercial) or non-compliance to federal regulations whether they are subject to or targeted by foreign influence or not.
The FBI has identified the following technology areas as having priority to unwanted foreign influence:
|
Information technology |
Energy-efficient and new-energy automobiles |
|
Computer numerical control machine tools and robotics |
Electric power equipment |
|
Aerospace Equipment |
New and Advanced Materials |
|
Marine engineering equipment and high-tech ships |
Biomedicine and high-performance medical instruments |
|
Advanced rail transportation equipment |
Agricultural equipment |
Within these technology areas and largely within STEM disciplines, the university has specific labs, federal agency programs, or technologies that contain Research Intellectual Property or Sensitive Research (defined above).
Each of the categories of research above have increasing levels of controls available to help mitigate risks of inadvertent disclosure or theft from foreign influence such as Technology Control Plans (TCP) or Research Security Plans (RSP). Many of these controls are put in place through normal university business procedures within the offices of research administration, however, not all research conducted at the university is procedurally reviewed or processed through those offices. Researchers should therefore consider these research categories and target areas in order to closely consider controls or safeguards they could utilize to protect their research data (see How to Safeguard Sensitive Research below).
Tools to Help Safeguard Intellectual Property and Sensitive Research
Information for proper electronic storage and transfer of research data and associated tools or platforms are available from the Data Privacy and Compliance Office. For any questions, contact the Data Privacy & Compliance Office at ua-privacy@alaska.edu.
The OGCAs can also help direct you to a Research Security Plan or Technology Control Plan that document a set of security protocols for sensitive research. RSPs are generally broad in scope and are intended to cover planned exchanges of research data or the conduct of research by specific persons or laboratories. TCPs are specific to information or materials that are controlled under export control laws. TCPs are more focused on protecting a specific item from access (physical or electronic) to prevent export control law violations (where a license may be required to access or export the controlled information).
Research Security Plan (RSP)
A Research Security Plan provides guidance and controls to researchers for sharing sensitive or controlled University information, such as unpublished intellectual property and research data. The RSP is also specific and tailored for planned or potential exchanges of information or collaboration. An RSP is not routinely prepared for all research or collaborative projects, they are used on an “as needed” basis which may be determined by university administration or researchers themselves. This determination is based on elevated concerns or the perception of risk (of theft or foreign influence), to protect the PI and other computers/researchers on UAF’s network from inadvertent or intentional unauthorized access.
Awareness of Insider Threats
n addition to traditional cyber security methods, such as phishing or hacking research systems, the FBI and the Department of State have identified certain techniques that have been used to access sensitive research information or intellectual property from university researchers:
- Sponsorship of foreign travel
- Study abroad opportunities
- Foreign conference or presentation opportunities
- Talent recruitment programs
- Gift or sponsored research funding
- publishing opportunities
- joint research opportunities
- In-kind research lab access or research personnel
These techniques may open opportunities of unwanted foreign influence by the inadvertent sharing or theft of intellectual property. This can occur by adversaries gaining access to university systems or research as a visiting scientist, student, or as lab personnel (Insider Threats), university researchers sharing of sensitive research data for collaboration or as requirements for gift/sponsored funding, or researchers unknowingly being subjected to cyber security theft when traveling abroad.
Insider Threats are identified as individuals that have legitimate or illegitimate access to research data, systems, or research personnel. The FBI has identified the following behaviors that may indicate someone as insider threat:
- Insistence on working in private
- Volunteers to help on sensitive work
- Unexplained or prolonged absences
- Freely searches through the files of others
- Requests for access that is not necessary
- Attempts to gain information without a need to know
- Failure to report oversea travel
- Takes research data or material from lab without authorization
- Violates security protocols
- Awkwardly utilizes audio or visual recording devices
- Maintaining data in unapproved or unmonitored systems.
- Maintaining independent or non-sanctioned electronic communication systems for work or research related purposes
The Department of State has training available on Insider Threats.
The techniques and behaviors above are meant to bring awareness for how research or intellectual property theft may occur in order to assist researchers in their diligence to mitigate foreign influence. These should not be considered as or used to create barriers to research collaborations and productivity. If concerns arise surrounding foreign influence, researchers should contact OGCA.
Federal agency actions related to Foreign Influence
- The National Institutes of Health (NIH) issued a Notice on March 30, 2018, reminding research institutions that PIs, sub-awardees and co-PIs must disclose all financial interests received from higher education or governmental institutions in countries outside the United States (NOT-OD-18-160).
- NIH Director Dr. Francis S. Collins issued a memo to institutions on Aug. 20, 2018, stating that the failure to properly disclose foreign relationships threatened to distort decision-making about the use of NIH funds.*
- The National Defense Authorization Act, signed in August 2018, included Sec. 1286, which stated that “The Secretary of Defense shall, in consultation with other appropriate government organizations, establish an initiative to work with academic institutions who perform defense research and engineering activities . . . to limit undue influence, including through foreign talent programs, by countries to exploit United State Technology ... ”*
- On March 20, 2019 the Department of Defense issued a memo explicitly outlining disclosure requirements for all key personnel listed on research and research-related educational activities supported by DoD grants and contracts*.
- NSF’s July 11, 2019 Dear Colleague Letter: Research Protection describes the emerging risks to the nation’s research enterprise by the actions of other governments to obtain sensitive research information. It also announces a new policy that NSF personnel and assignees under an IPA cannot participate in foreign government talent recruitment programs.
- The National Science Foundation issued a statement on “Security and Science” dated October 23, 2018, stating that US universities must “embrace transparency and rigorously adhere to conflict of interest and conflict of commitment policies.”*
- The Department of Energy issued a directive dated June 7, 2019, mandating that “federal and contractor personnel fully disclose and, as necessary, terminate affiliations with foreign government-supported talent recruitment programs” on new DOE contracts and subcontracts. DOE is expected to issue a separate policy directive to implement the requirement on DOE grants and cooperative agreements*.
- As a reminder, NASA has long-standing restrictions on using NASA funds to enter into agreements “to participate, collaborate, or coordinate bilaterally in any way with China or any Chinese-owned company, at the prime recipient level or at any subrecipient level, whether the bilateral involvement is funded or performed under a no-exchange of funds arrangement” (grant restrictions, contract restrictions)*.
- The Federal Bureau of Investigation (FBI) issued a paper CHINA: The Risk to Academia that describes some of the Chinese government’s initiatives to conduct economic espionage in academia. This paper provides resources for identifying specific target areas of foreign adversaries and useful tips and practices to assist researchers in identifying insider threats.
*Courtesy Pennsylvania State University
Federal Agency Disclosure Requirements for Current, Pending, & Other Support
NIH DISCLOSURE REQUIREMENTS
NIH Notice (NOT-OD-19-114): Reminders of NIH Policies on Other Support and on Policies related to Financial Conflicts of Interest and Foreign Components. This notice and the accompanying FAQs for Other Support are a significant change in policy interpretation. Faculty funded by or submitting to NIH must read this notice and FAQs closely to determine if additional disclosures should be made at JIT or in their next progress report. Various professional organizations are actively communicating with NIH on the concerns and impact this notice will have. We will share any developments that may arise, however, the notice is in effect and we must comply. Below is a summary of the current policy:
- Foreign Components: NIH requires investigators to disclose whether the project includes a “foreign component”. If it does, the application must include a foreign justification document and NIH must approve the “foreign component” in the project. NIH defines a foreign component as: The performance outside of the United States, either by the recipient or by a researcher employed by a foreign organization, of any significant scientific element or segment of a project, whether grant funds are expended outside the United States or not. Activities that meet this definition of “foreign component” include, but are not limited to,
- the involvement of human subjects or animals,
- extensive foreign travel by recipient project staff for the purpose of data collection, surveying, sampling, and similar activities,
- any activity of the recipient that may have an impact on U.S. foreign policy through involvement in the affairs or environment of a foreign country.
Examples of other grant-related activities that may be of significance to NIH and should be disclosed are:
- collaborations with investigators at a foreign site anticipated to result in co-authorship;
- use of facilities or instrumentation at a foreign site; or
- receipt of financial support or resources from a foreign entity.
NIH does not consider foreign travel for consultation to be a “foreign component”.
- Requirements During the Award:
The Research Performance Progress Report (RPPR) must include all persons who have worked on the project at least one-person month per year during the reporting period, regardless of the source of their compensation. Investigators must indicate if such a person’s primary affiliation is with a foreign organization unless the individual is working on the award solely while in the United States.
Adding a Foreign Component -
NIH requires prior approval to add a “foreign component” not included in the application
and approved at time of award.
NSF DISCLOSURE REQUIREMENTS
NSF’s draft Proposal and Award Policies and Procedures Guide (PAPPG – page II-23) contains revisions to Current and Pending Support (chapter II.C.2.h) and supporting NSF comments that clarify the expectation faculty should disclose outside or individual activities that may not be part of the work activities performed on behalf of their institution. Although these clarifications are not in effect yet, faculty are encouraged to consider these statements carefully as to NSF’s intent for broader disclosure of activities in Current and Pending Support. Here again professional organizations are seeking further clarity from NSF as the statements appear to be new interpretation that will change previous disclosure practices. Excerpts of this draft are as follows:
- Page II-23 (h) Current and Pending Support (revisions emphasized):
Current and pending support information must be separately provided for each individual designated as senior personnel on the proposal through use of an NSF-approved format. Information must be provided about all current and pending support, including this project, for ongoing projects, and for any proposals currently under consideration from whatever source, irrespective of whether such support is provided through the proposing organization or is provided directly to the individual. All projects and activities, current or proposed that require a time commitment from the individual must be reported, even if the support received is only in kind (such as office/laboratory space, equipment, supplies, employees, students). The total award amount for the entire award period covered (including indirect costs) must be provided, as well as the number of person-months (or partial person-months) per year to be devoted to the project by the senior personnel involved.
- In addition, the following NSF comments were provided:
- Information must be provided for all current and pending support irrespective of whether such support is provided through the proposing organization or directly to the individual.
- Examples of current and pending support have been expanded to include non-profit organizations and consulting agreements.
- All projects and activities that require a time commitment must be reported (no minimum has been established), even if the support received is only in-kind.
OTHER AGENCIES (general guidelines)
Other Support:
Proposers must submit the following for all key personnel, whether or not the individuals’ efforts under the project are to be funded through the award:
- Previous (award period of performance ending within the past 5 years), current, and pending research support including:
- Title
- Time commitments
- Supporting agency
- Name and address of funding agency’s procuring contracts/grants officer
- Performance period
- Level of funding
- Brief description of project goals
- Specific aims
- Identify any overlap with other existing and pending research projects or state there is no overlap
Foreign Component:
Identify any partner organizations and their contribution(s), including location/country of the partner.
Disclosures to the Public
Disclose all financial relationships related to your research in all public sharing of your research results, such as in presentations, publications or otherwise. It is important to note that journal disclosure requirements are often broader than UAF requirements, which may require additional disclosures.
Where to Get Assistance
|
Disclosure Type |
Contact |
|
Grant Proposal, Other Support & Foreign Components |
Office of Grants and Contracts Administration (OGCA) |
|
UAF Financial Interest Disclosures |
Office of Research Integrity (ORI) |
|
UA Outside Activities Disclosures |
University of Alaska Statewide
|
|
Foreign Travel |
Office of Research Integrity (ORI) |
|
Export Control |
Office of Research Integrity (ORI) |
Foreign Travel Guidance
- For any travel conducted based on your role, title, or work at UAF, a travel authorization (TA) should be completed to document the trip. This helps to document the trip as being business related and in doing so can provide insurance coverage. This is particularly important to capture when an outside entity is covering the cost of travel through UAF or directly to you. If you receive direct reimbursement for travel, and that reimbursement exceeds your expenses, you may need to report outside consulting / compensation and it may constitute as reportable income for personal tax purposes.
- Follow applicable guidelines for travel to any foreign (international) location. From time to time, situations arise that make certain locations more or less high-risk, including restricted regions. Be sure to consult UAF’s s Travel Office as you plan your trip and before you leave for current information. The US Government also periodically issues travel advisories and alerts.
- Cybersecurity is of critical importance when traveling internationally. For information on data security while traveling, review the Department of Homeland Security’s “Cybersecurity While Traveling Tip Sheet” and the Center for Internet Security’s “Cybersecurity While Traveling”.
- Do not take or ship ahead anything that is controlled for export without a license unless it is covered by a license exception (email ORI for assistance). If you are presenting or discussing research, only provide information that is either already published or has no restrictions on publication.
- OGCA can perform routine checks and clearances for foreign entities and individuals as required in part by our funding rules and regulations, and applicable legal requirements of the US federal government, to help protect UAF institutionally, and faculty travelling, from inadvertent violations of export control laws and regulations. Contact OGCA for assistance.
- Please be aware that, as with any UAF faculty researcher, staff or employed student, and regardless of funding source or location of the person with whom you are disclosing information, best practices for information security require that an individual who does not have a business relevant reason to know something that is being protected, or should protect information, should not be given unrestricted access to disclosed information. This includes that, from time to time, confidentiality may be needed in your collaboration with any entity or individual, and of course not limited to foreign travel or collaboration. UAF has posted general guidance on confidentiality (NDAs).
Lobbying and Earmarks
Federal regulations prohibit the use of federal grant or contract funds for the purpose of lobbying. Because tax and political compliance laws impose restrictions, and even prohibitions, on certain political activities and on the use of resources, buildings and equipment at a non-profit institution such as UAF, any such activities must be in compliance with these legal requirements.
Applicable laws dictate that no person may engage in any political activity in support of or opposition to any candidate for elective public office on behalf of UAF or use any UAF resources for such a purpose. Similarly, no person may lobby on behalf of UAF or use UAF's name or resources to lobby any federal, state, or local legislative or administrative official or staff member unless specifically authorized to do so by UAF. Individuals taking personal political positions must clearly indicate that they are acting as an individual and not on behalf of UAF.
UAF endorses the well-established peer review systems of our sponsors to identify proposals worthy of funding.
Faculty may not become involved in attempts to influence federal, state or local legislation or draft legislation that includes funding intended for a specific UAF project ("earmarks"). This includes any efforts to circumvent applicable merit-based or competitive allocation processes.
Mandatory Disclosures of Violations of Criminal Law
Per 2 CFR Part 200, §200.113 (see full text below), the University of Alaska Fairbanks is obligated to disclose any violations of Federal criminal law involving fraud, bribery, or gratuity violations potentially affecting the Federal award. The OGCA should be notified in a timely manner in the event of any such violations.
- 200.113 Mandatory Disclosures
The non-Federal entity or applicant for a Federal award must disclose, in a timely manner, in writing to the Federal awarding agency or pass-through entity all violations of Federal criminal law involving fraud, bribery, or gratuity violations potentially affecting the Federal award. Non-Federal entities that have received a Federal award including the term and condition outlined in Appendix XII—Award Term and Condition for Recipient Integrity and Performance Matters are required to report certain civil, criminal, or administrative proceedings to SAM. Failure to make required disclosures can result in any of the remedies described in §200.338 Remedies for noncompliance, including suspension or debarment. (See also 2 CFR part 180, 31 U.S.C. 3321, and 41 U.S.C. 2313.)
No-Cost Extensions
If project work is on-going and funds remain available to cover project expenses, it may be appropriate to request an extension of the project period. Considerations include award terms, funding for committed effort on the project, timing, and approvals required.
Under the Federal Demonstration Partnership (FDP), UAF is authorized to approve a single no-cost extension (NCE) of up to 12 months on eligible federal grants, provided it notifies the sponsor that it has elected to take such an extension, explains why the extension is needed, and provides the notification at least 10 days before the expiration date specified in the award.
A formal request to the sponsor may be required if the sponsor is not a member of the FDP, is a non-federal sponsor, or if this is not the first NCE requested for an award. The award's terms and conditions apply.
If an NCE is needed, an AwaRE form will need to be submitted with the following award and extension justification information:
Award Information
- Project Number
- Award Number
- Current Period of Performance
- Requested Extension End Date
Justification for Extension
- Brief reason for the extension, including the reason(s) the project was not completed within the original period of performance.
- Brief summary of work to be accomplished during the extension period.
- Amount of funds expected to be available on the current end date and the intended use during the extension period.
- If applicable, any updated compliance documents (IRB/IACUC/IBC data).
- The request will be submitted according to the procedures of the sponsoring agency. With some sponsors the request will be submitted through an online system, such as FastLane, NSSC, or eRA Commons. In other situations a request will be submitted via e-mail to the grants official. Please note that there are deadlines for submitting these requests, which will vary according to sponsor requirements.
If additional funding is required, this will still be prepared as an extension (i.e., a modification), but will not be no cost and will require an OGCA analyst to review your budget.
Personnel Changes
Since the approval of the project has been, to some degree, based on the participation or qualifications of the PI and other key personnel, the sponsor requires notification whenever there is to be a significant change in the level of participation in the awarded project by the Principal Investigator (PI). The sponsor has the option to either approve or disapprove of any proposed alternate plans related to the research.
A significant change in the level of participation may be defined as:
- The PI not giving active direction of the project for a continuous period of time greater than three months, (e.g., on sabbatical leave), or
- A change of 25% or greater in the level of committed effort, or
- A withdrawal from the project.
For non-federal sponsors, review the specific award’s terms and conditions.
The request should be initiated on the AwaRe form. The program officer at the awarding agency must be notified in a letter signed by the PI and a UAF Authorized Organizational Representative (AOR). The letter should detail the reason for the change in key personnel and provide the replacement PI's curriculum vitae. These requests must be made prior to implementing any changes. UAF will make the appropriate changes to award files and financial records once written approval has been received from the sponsor.
Specific Federal Agency Information For Significant Changes of Personnel or PI
- National Science Foundation (Located under Chapter II.B.2.a-h)
- National Institutes of Health (8.1.2. Prior Approval Requirements)
- US Department of Agriculture, NIFA (XIII. PRIOR WRITTEN APPROVAL)
Protection of Confidential or Proprietary Proposal Information
Proposals sometimes contain confidential or proprietary information that is required in order to support a proposed scope of work. When confidential or proprietary information is included in an application to a federal government agency, it is with the understanding that the information will be used or disclosed only for evaluation of the application. However, if a grant is awarded as a result of or in connection with an application, the proposal becomes a public record and will be released if requested under provisions of the Freedom of Information Act and Privacy Act.
Confidential or proprietary information included in a research proposal should always be clearly identified with an appropriate legend, which can be obtained from OGCA.
Safeguarding Confidential Information
There are multiple ways in which confidentiality terms can be agreed to by UAF. They can exist within agreements for sponsored research, purchase of instruments or services, licenses, material transfer, collaboration etc. or they can be the purpose of a standalone agreement such as a Non-Disclosure Agreement (NDA). The following offices are authorized to review, negotiate, and execute these agreements by an authorized official:
|
Purpose / Agreement Type |
Office to Review |
|
Discussions involving Sponsored Projects |
OGCA |
|
Other Research - Discussions related to research collaborations |
OGCA |
|
Discussions related to licensing/commercialization/Intellectual Property |
OIPC |
|
Other (Not Research) – Purchase of equipment or services |
OGCA |
Confidential information can be owned and maintained by UAF or received from, and owned by, an external party. NDAs or confidentiality terms in agreements help to identify and define the confidential information subject to the agreement and govern the exchange of the confidential information between the parties and the responsibility of each party to prevent inappropriate disclosure. UAF faculty and staff (including graduate students and undergraduate students employed by UAF) possessing confidential information, whether owned by UAF or received from a third party, have a personal responsibility to know and understand confidentiality terms and to safeguard such confidential information.
This guidance is intended to assist UAF faculty and staff in safeguarding sensitive research data and confidential information. Additional requirements may apply while traveling abroad or for specific foreign research collaborations (see last bullet point on Foreign Influence).
NEVER SIGN AN AGREEMENT YOURSELF
- FIRST, NEVER SIGN AN AGREEMENT YOURSELF: This is for your and UAF’s protection. There is no such thing as a “standard” NDA that an outside third party (such as a vendor or prospective sponsor) will give you. Additionally, only authorized UAF officials that have a written delegation of signature authority from the President can execute agreements on behalf of UAF. Nearly all faculty and staff are not authorized to sign an NDA or an agreement that binds the institution. However, the offices above will coordinate with employees to review and approve content or confidentiality terms as part of the negotiation process.
UNDERSTAND CONFIDENTIALITY MARKING
- Make sure you clearly understand what information is confidential pursuant to particular agreement terms and what will not be.
- UAF conforms all confidentiality clauses to require all confidential information from a discloser to be clearly marked as confidential. Specifically, (i) written or tangible confidential information provided by a discloser must be labeled “confidential” or equivalent (such as “proprietary”, or “secret”), and (ii) information communicated any other way (such as verbally or visually) by a discloser, must be identified as confidential at time of disclosure and reduced to writing within 30 days of the disclosure with a written summary.
PROTECT YOUR ABILITY TO PUBLISH
- Make sure that the requested confidentiality obligations will not make it difficult for you to publish the results of your research, or will not affect other research or academic work you may be doing. Watch out especially for impact on students. As an educational institution, UAF cannot and will not risk a student losing the ability to complete and publish a dissertation, thesis, or other academic work needed for a degree. We may agree to certain redactions in publications for protecting confidential information owned by a third party, however, the students, faculty and PI must clearly understand and accept these before agreeing to receive confidential information with such limitations.
SECURE PHYSICAL AND ELECTRONIC PROTECTION
- Make sure you have, or have requested and will have in place before receiving confidential
information, the needed and appropriate means to maintain confidential information.
Confidentiality means you and your team must actually keep disclosed confidential
information protected and not generally available to other personnel or the public.
There are physical protections (such as lab doors with limited card reader or keyed
access, locked file cabinets, or having conversations behind closed doors) and electronic
(digital) protections (such as password protected computers or email encryption).
Keep your own notes and print-outs, and digital or electronic content, and tangible
marked materials, confidential to the extent they contain confidential information.
If you share laboratory facilities, or have laboratory facilities open to others,
store confidential material away in a secure location, with access limited to authorized
personnel only. Your computer and IT system (information received and stored electronically)
must use customary security measures, including encryption if allowed or required
by UAF policy.
Equipment maintained by UAF’s Office of Information Technology (OIT) is typically compliant, but sometimes additional measures are required depending on circumstances. Contact OIT if you have IT questions, at helpdesk@alaska.edu or https://www.uaf.edu/nooktech/.
RESPECT SHARING AND USE LIMITS
- Share confidential information only on a need-to-know basis. Mark and maintain received and disclosed confidential information as “confidential”. Tell UAF recipients what is confidential before sharing. Do not share outside UAF.
- Respect use limits. Only use the confidential information for the purpose that is specified in the NDA, and not for any other purpose. If you discover that confidential information has been accessed by an unauthorized person, you must immediately notify the UAF authorized official who signed the NDA so that proper notification can be provided to the party who disclosed to you.
- Note that confidentiality obligations continue after a project or an agreement expires, commonly for years. Most often at UAF, confidentiality obligations continue for 1 to 2 years after expiration of the agreement. In some cases, obligations to maintain confidentiality could continue for as long as 3 to 5 years, or rarely, more, if project needs require.
EXPORT CONTROL MAY BE ADDITIONALLY NEEDED
- Note that confidentiality terms typically only allow exchange of confidential information that is NOT export controlled. While non-confidential information, and nearly all confidential information, disclosed to UAF generally is not subject to export controls, if a discloser proposes information may be (or will be) export controlled, you will need a Technology Control Plan (TCP) finalized and in place, and signed by all who will receive, BEFORE receipt of any export-controlled information. Contact Regulatory Services for export control compliance. Your TCP likely will contain additional instructions beyond those commonly used for confidentiality. Receiving export-controlled information without an export control compliance plan in place, could cause you or members of your team, to violate criminal law.

