Records Retention & Management
The University of Alaska Fairbanks maintains a wide variety of records in both paper and electronic forms. These records are essential to the mission of UAF and must be created, maintained and destroyed according to the policies established by the UA Board of Regents. These policies and regulations are available on the UA Records and Information Management (RIM) website.
Not all documents received, utilized or distributed by UAF are considered university records. Most records considered official university records are listed on the Retention and Disposition Schedules distributed by UA RIM. The schedules outline the types of documents considered university records along with the overall life cycle for each. Retention schedules are available for several functional areas including
- Admissions & Registration
- Finance
- Financial Aid
- Human Resources
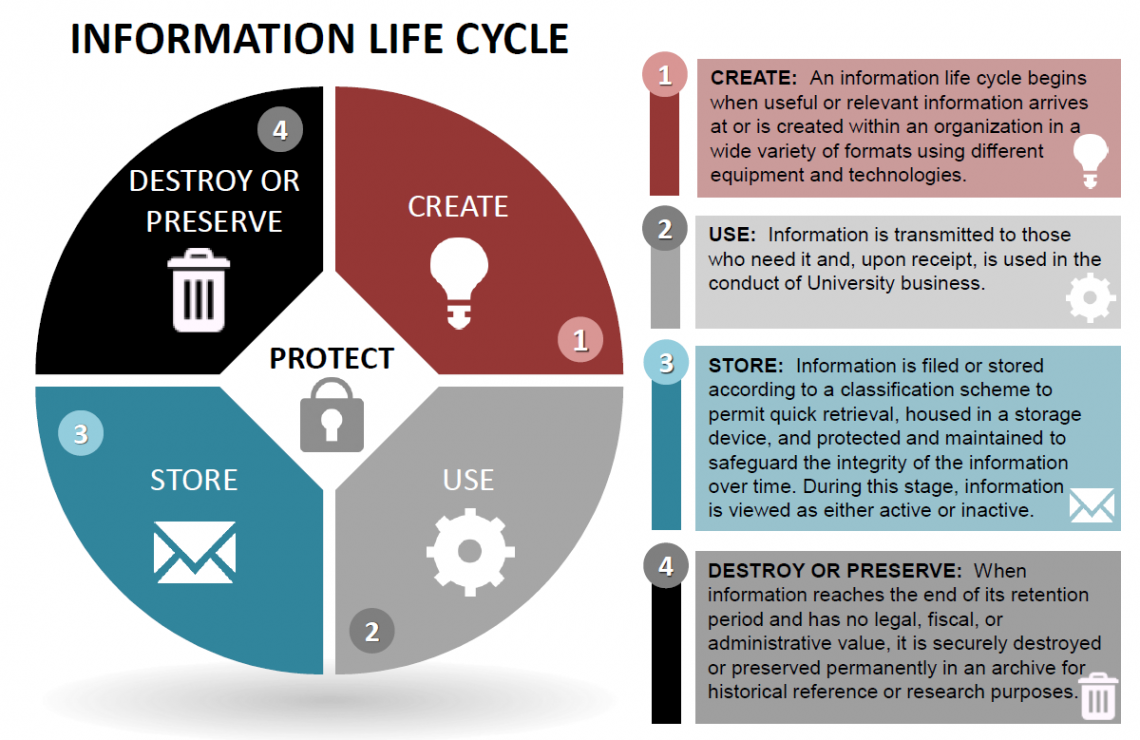
University records are part of the overall Information Management (IM) process at UAF. In the IM life cycle (as shown in this info graphic), attention is paid to tracking and taking care of document records during the time of creation or reception by UAF, usage to support the UAF mission, storage and destruction (if appropriate).
UA uses the OnBase Enterprise Content Management (ECM) System from Hyland Software as the official repository for all UAF records along with many other UAF documents that need tracking and maintaining. Each UAF functional area (HR, Finance, Student Services, etc.) uses OnBase for at least some of their records. There are also ongoing projects to increase the types of document records migrated to the OnBase system.
In areas where OnBase is not used, take care throughout the IM process to ensure the handling of documents meets UA requirements for the confidentiality, integrity and availability of those documents. Visit the UA RIM website for more information.
Please contact the UAF OnBase Administrator to discuss using OnBase to help maintain department documents and records.
Access Method
There are several ways to access OnBase. Please use the descriptions below to determine the method that will best meet your needs.
- Unity Client - Our recommended client for Windows users. Unity looks and behaves much like other Office applications and should have better performance for users on slower network connections.
- Web (Thin) Client - A web application usable on Macintosh and Windows systems. It supports most current browsers including IE, Edge, Chrome, Firefox and Safari. We recommend the web client if occasionally looking up documents in OnBase and do not need to do much importing or workflow.
- OnBase (Thick) Client - For OnBase administration or specific users on Windows who do a lot of batch processing or auto-indexing. We do not recommend the install/use of Thick Client unless there is a specific need for it. Please note that as of version 24.1, WorkFlow can no longer be accessed from Thick client.
Most UAF users should use either Unity or the Web client. If neither of these meet your needs, please contact the UAF OnBase Administrator for further information regarding Thick Client use (installed on request).
Visit the OnBase Landing Page to access the Web Client or to obtain the Unity installer. Note that Unity is also available in the Software Center for UA Windows systems. While the installers for Thick client and Disconnected Scanning are also available from the landing page, please contact the OnBase team prior to attempting to install them as there are several configuration steps needed and (in the case of Disconnected Scanning) a separate license.
Access Approval
Access to functional areas in OnBase is granted upon the request of the appropriate security coordinator. Normally, the procedure is for the coordinator to go to the OIT Service Catalog and click on the "OnBase Access Request" button. This will bring up a page that lists all of the combinations of permission groups. There is an OnBase Security Group Help Page available. While we cannot take applications from users for their own access, supervisors are welcome to request access for their employees. Some accesses require validating the request with a coordinator before granting access.
UAF Security Coordinators
Please click here for a current list of Campus Security Coordinators by functional area.
It is important to note that UAF does not normally keep records indefinitely. Every document has a defined life cycle and is eventually eligible for destruction. Documents under audit or otherwise subject to legal review are not destroyed until such time as the review or audit is completed and the document is at the end of its life cycle.
There are many different ways to destroy documents. It is important to track when, how and by whom this destruction was accomplished. Tracking for UAF documents is done with the Certificate of Destruction (COD) and (if needed) COD Continuation Sheets. The COD forms are intended for use as collections of documents are destroyed. It is up to each department to determine what defines a "collection" of documents and how these collections are tracked. Some departments will track individual personnel folders while others might have a shared volume that has scanned receipts in it and all receipts are purged monthly. Your department should document what constitutes a collection for the records it maintains.
Even though the department has copies of records, it might not be the home for those records. For example, grant documentation belongs to OGCA. The official copies are maintained by OGCA even if a PI has a copy of their own grant documentation. Copies of records given to departments for reference do not need to be included in the COD. Only the official copies are required on the COD.
Departments that have records requiring tracking on a COD should keep a running copy of that COD and fill it in as collections are destroyed. Enter the following information each time:
- The date a collection was destroyed
- The type(s) of records in the collection
- How the collection was destroyed
- Any identification (UAID, series #, month, etc) for the collection destroyed
- The initials of the person doing the destruction
At the end of the fiscal year, the designated records person at the department should sign and date any completed or in-progress CODs and then file them for future review.